고정 헤더 영역
상세 컨텐츠
본문
-->
- Generate Ssh Key Windows Server
- Generate Public Key For Windows
- Generate Ssh Key Windows Cmd
- Generate Public Key Windows Server Free
To install the public key, Log into the server, edit the authorizedkeys file with your favorite editor, and cut-and-paste the public key output by the above command to the authorizedkeys file. Save the file. Configure PuTTY to use your private key file (here keyfile.ppk). Then test if login works. How to generate an SSH key and add your public key to the server for authentication Step 1: Check for SSH Keys. First, check for existing SSH keys on your computer. Step 2: Generate a new SSH key. With your command line tool still open, enter the text shown below. Step 3: Add your key to the.
Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
It has all the Arabic alphabets. Inpage 2009 free download for mac. Newer and stylish fonts with modern looks were added, and more language features for Urdu and Punjabi writing was added. All the offline and standalone setup files have been updated to the latest version. It also includes version 3.0.5 along with compatibility for x86 and x64 environments. Many Arabic words were added and new user interfaces with easier to navigate buttons and menus.
Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
The private key (www.hostname.com.key) is stored locally on the server and is employed for decryption. The public key, in the form of a WildCard SSL Certificate Signing Request (certrequest.csr. Wildcard 256 generate key openssl code. Sep 26, 2018 This article is an end-to-end demonstration of steps to build a CSR for wildcard SSL certificates using OpenSSL and then a complete process of installation of. Which symmetric encryption will be chosen by SSL depends only on what the server/client support, not on the key size of the certificate. You need to fix the server. Jun 07, 2017 The code snippet. “How to generate a wildcard cert CSR with a config file for OpenSSL” is published by pascal.brokmeier in curiouscaloo.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.
See also
Overview
Public key authentication is a way of logging into an SSH/SFTP account using a cryptographic key rather than a password.
Generate Ssh Key Windows Server
If you use very strong SSH/SFTP passwords, your accounts are already safe from brute force attacks. However, using public key authentication provides many benefits when working with multiple developers. For example, with SSH keys you can
- allow multiple developers to log in as the same system user without having to share a single password between them;
- revoke a single developer's access without revoking access by other developers; and
- make it easier for a single developer to log in to many accounts without needing to manage many different passwords.
How Public Key Authentication Works
Keys come in pairs of a public key and a private key. Each key pair is unique, and the two keys work together.
These two keys have a very special and beautiful mathematical property: if you have the private key, you can prove you have it without showing what it is. It's like proving you know a password without having to show someone the password.
Public key authentication works like this:
- Generate a key pair.
- Give someone (or a server) the public key.
- Later, anytime you want to authenticate, the person (or the server) asks you to prove you have the private key that corresponds to the public key.
- You prove you have the private key.
You don't have to do the math or implement the key exchange yourself. The SSH server and client programs take care of this for you. https://brownscreen919.weebly.com/sketchup-3d-free-download-for-mac.html.
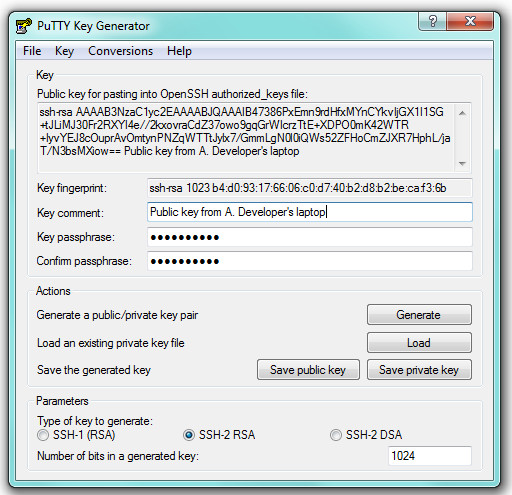
Generate an SSH Key Pair
You should generate your key pair on your laptop, not on your server. All Mac and Linux systems include a command called ssh-keygen that will generate a new key pair.
If you're using Windows, you can generate the keys on your server. Just remember to copy your keys to your laptop and delete your private key from the server after you've generated it.
To generate an SSH key pair, run the command ssh-keygen.
It will look like this when you run it:
You'll be prompted to choose the location to store the keys. The default location is good unless you already have a key. Press Enter to choose the default location.
Next, you'll be asked to choose a password. Using a password means a password will be required to use the private key. It's a good idea to use a password on your private key.
After you choose a password, your public and private keys will be generated. There will be two different files. The one named id_rsa is your private key. The one named id_rsa.pub is your public key.
You'll also be shown a fingerprint and 'visual fingerprint' of your key. You do not need to save these. https://sinamislif.tistory.com/8.
Configure an SSH/SFTP User for Your Key
Method 1: Using ssh-copy-id
Now that you have an SSH key pair, you're ready to configure your app's system user so you can SSH or SFTP in using your private key.
Photoshop cs6 cracked version. To overcome this issue, Adobe launched a complete package known as Adobe Master Collection.
To copy your public key to your server, run the following command. Be sure to replace 'x.x.x.x' with your server's IP address and SYSUSER with the name of the the system user your app belongs to.
Method 2: Manual Configuration
If you don't have the ssh-copy-id command (for example, if you are using Windows), you can instead SSH in to your server and manually create the .ssh/authorized_keys file so it contains your public key.
Generate Public Key For Windows
First, run the following commands to make create the file with the correct permissions.
And “ Deep Scan” assures up to 100% of the lost data recovery by using file signatures.The laundry list of data recovery capabilities is just enormous—, Time Machine support, encrypted and corrupt hard drive recovery, Boot Camp Partition recovery, and recovery from inaccessible drives/volumes. The software does it all. But that’s not all yetthese features can be actualized via a super-easy graphical DIY interface that allows customization of key data-scan parameters including drive area selection, type of data, and file format. Best sd recovery software mac. “ Can’t Find Volume” ensures you recover lost APFS/HFS+ partitions and the inaccessible data in them.
https://sinamislif.tistory.com/19. Adding 20 cd-keys per a day day 1 hj8z-td8w-d288-np8t 26dg-x66n-9mcd-xjbw ckmz-k7xt-z9tw-xwp2 chpg-wd8h-8z7t-64mk f488-9d7m-efjc-k9n7 m2zv-zgxt-v876-rm2h. Serial key for Diablo 2 can be found and viewed here. We have the largest serial numbers data base. KeyGenNinja.com (former KeygenGuru) KEYGENNINJA.COM IS THE BEST WAY TO FIND CRACKS, SERIAL NUMBERS, KEYGENs: Forum moderators are required!!! Free diablo ii cd keys LAST CHECK:!!-Remember that everyone who use these cd-keys will be using these cd keys on battle.net, So if you find.
Next, edit the file .ssh/authorized_keys using your preferred editor. Copy and paste your id_rsa.pub file into the file.
Log In Using Your Private Key
You can now SSH or SFTP into your server using your private key. From the command line, you can use:
If you didn't create your key in the default location, you'll need to specify the location:
If you're using a Windows SSH client, such as PuTTy, look in the configuration settings to specify the path to your private key.
Granting Access to Multiple Keys
The .ssh/authorized_keys file you created above uses a very simple format: it can contain many keys as long as you put one key on each line in the file.
If you have multiple keys (for example, one on each of your laptops) or multiple developers you need to grant access to, just follow the same instructions above using ssh-copy-id or manually editing the file to paste in additional keys, one on each line.
When you're done, the .ssh/authorized_keys file will look something like this (don't copy this, use your own public keys):
However, It also support contemporary and more advance functions. Above all, it allows you to uninstall programs and support elimination issues. Autocad 2006 key generator free download. software. For the reason that, It will also offer you more flexible option to get related to a cloud account or cell gadgets.
Additional Information
Retrieve Your Public Key from Your Private Key
The following command will retrieve the public key from a private key:
This can be useful, for example, if your server provider generated your SSH key for you and you were only able to download the private key portion of the key pair.
Idealistic is just starting her first teaching job, that as freshman and sophomore English teacher at Woodrow Wilson High School, which, two years earlier, implemented a voluntary integration program. The freedom writers diary pdf free download torrent.
Google news for macos. Note that you cannot retrieve the private key if you only have the public key.
Correcting Permissions on the .ssh Directory
The instructions in this article will create your server's .ssh directory and .ssh/authorized_keys file with the correct permissions. However, if you've created them yourself and need to fix permissions, you can run the following commands on your server while SSH'd in as your app's system user.
Disabling Password Authentication
NOTE: When changing anything about the way SSH is accessed(ports, authentication methods, et cetera), it is very strongly recommended to leave an active root SSH session open until everything is working as intended. This ensures you have a way to revert changes in the event something goes wrongand logins are not working properly.
As an extra security precaution, once you have set up SSH keys, you may wish to disable password authentication entirely. This will mean no users will be able to log into SSH or SFTP without SSH keys. Anyone entering a password will receive a message like:
Or:
The shell command to change key bindings is bindkey, Backspace presumably sends byte 127 (^?; check by typing Ctrl+V then Backspace), and the edition command to delete a character backwards is backward-delete-char. What key combination generates a backspace character in unix. The Linux kernel default lets Ctrl-Backspace generate BackSpace - this is sometimes useful as emergency escape, when you find you can only generate DELs. The left Alt key is sometimes called the Meta key, and by default the combinations AltL-X are bound to the symbol MetaX.
Generate Ssh Key Windows Cmd
Disabling password authentication is an excellent way to improve server security. Please see our guide here for the steps to accomplish this goal.
Generate Public Key Windows Server Free
Then, test whether you're able to log in with a password by opening a new SSH or SFTP session to the server. Passwords should not be able to be used and, if everything has been done correctly, an error will be issued when someone tries to use a password. Unless this setting is changed back to allow password authentication, no users will be able to log in without an SSH key set up.




